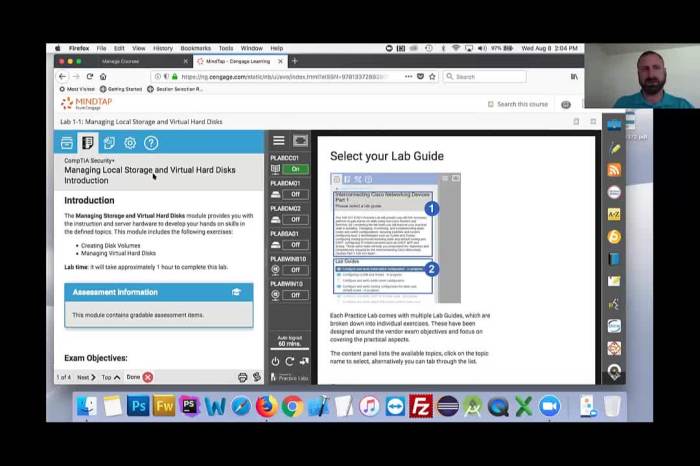
Live virtual machine lab 3.2: module 03 determining security vulnerabilities – In the realm of virtual machine security, Live Virtual Machine Lab 3.2: Module 03 emerges as a beacon of knowledge, guiding us through the intricacies of identifying and mitigating security vulnerabilities. This module delves into the methodologies, types, and consequences of vulnerabilities, empowering us with the tools and strategies to safeguard our virtual environments.
As we navigate the ever-evolving landscape of cybersecurity, understanding the nuances of virtual machine security becomes paramount. This module provides a comprehensive exploration of the subject, equipping us with the knowledge and skills necessary to protect our critical data and systems.
1. Introduction to Live Virtual Machine Lab 3.2
Module 03
This module introduces the concepts and techniques for identifying and mitigating security vulnerabilities in virtual machine (VM) environments. Virtualization has become a critical component of modern computing, providing benefits such as resource consolidation, isolation, and flexibility. However, VMs also introduce new security challenges that must be addressed to ensure the confidentiality, integrity, and availability of data and systems.
This module covers various methods for determining security vulnerabilities in VMs, including manual and automated approaches. It also discusses the different types of security vulnerabilities commonly found in VM environments, their potential impact, and real-world examples of security breaches caused by vulnerabilities.
2. Methods for Determining Security Vulnerabilities, Live virtual machine lab 3.2: module 03 determining security vulnerabilities
There are several methods for identifying security vulnerabilities in VMs. These methods can be broadly classified into two categories: manual and automated.
- Manual methodsinvolve manually inspecting the VM configuration, guest operating system, and applications for potential vulnerabilities. This can be a time-consuming and error-prone process, but it can be effective in identifying vulnerabilities that may be missed by automated tools.
- Automated methodsuse software tools to scan VMs for vulnerabilities. These tools can be used to quickly and efficiently identify a wide range of vulnerabilities, including missing patches, insecure configurations, and malicious software.
3. Types of Security Vulnerabilities
There are many different types of security vulnerabilities that can affect VMs. These vulnerabilities can be classified into several categories, including:
- Configuration vulnerabilitiesoccur when the VM is not properly configured. This can include insecure default settings, misconfigurations, or lack of necessary security controls.
- Software vulnerabilitiesoccur when the guest operating system or applications running on the VM contain vulnerabilities. These vulnerabilities can be exploited by attackers to gain access to the VM or its data.
- Network vulnerabilitiesoccur when the VM is exposed to network attacks. This can include attacks on the VM’s network interface, the virtual switch, or the underlying physical network.
- Hypervisor vulnerabilitiesoccur when the hypervisor software that manages the VM is compromised. This can allow attackers to gain control of the VM or the entire virtualized environment.
4. Mitigation and Remediation Strategies
There are several best practices that can be implemented to mitigate and remediate security vulnerabilities in VMs. These practices include:
- Patchinginvolves installing security updates to fix known vulnerabilities in the guest operating system and applications.
- Configuration hardeninginvolves configuring the VM to reduce the risk of exploitation. This includes disabling unnecessary services, setting strong passwords, and enabling security features such as firewalls and intrusion detection systems.
- Intrusion detection systemscan be used to detect and respond to security attacks. These systems can be configured to monitor network traffic, file system activity, and other system events for suspicious activity.
5. Case Study
This module concludes with a case study of a security vulnerability assessment conducted on a live VM. The case study walks through the steps involved in the assessment process, from vulnerability identification to remediation. The results of the assessment are analyzed, and recommendations are provided for improving security.
Expert Answers: Live Virtual Machine Lab 3.2: Module 03 Determining Security Vulnerabilities
What are the key objectives of Live Virtual Machine Lab 3.2: Module 03?
This module aims to provide an in-depth understanding of security vulnerabilities in virtual machine environments, enabling learners to identify, assess, and mitigate potential threats.
What are some common methods for determining security vulnerabilities in virtual machines?
Various methods are employed, including vulnerability scanning, penetration testing, and code analysis, each with its strengths and limitations.
How can organizations mitigate and remediate security vulnerabilities?
Best practices include implementing patching and update mechanisms, hardening system configurations, and deploying intrusion detection systems.